In today's cloud age, with data fragmenting and IT resources becoming increasingly strained, cyber threats are a growing concern for all organisations. While traditional data protection measures remain vital, they often feel reactive rather than proactive. Commvault, however, is shifting this narrative, developing a dynamic, proactive defence against cyber threats.
What impresses me about Commvault's strategy, particularly compared to other vendors, is their blend of data protection and security. By merging these two key aspects, Commvault's platform evolves from a 'last resort' recovery solution to an active shield against potential cyber threats.
This approach was discussed during Commvault's recent online event, "Accelerating Cyber Defence and Response with Next Generation Data Protection". CEO, Sanjay Mirchandani, outlined several thought-provoking points that underline Commvault's proactive and integrated approach to cyber defence:
The dual implications of AI, arming both defenders and adversaries with advanced tools.
The complexity and vulnerabilities of using various tools to protect cloud data.
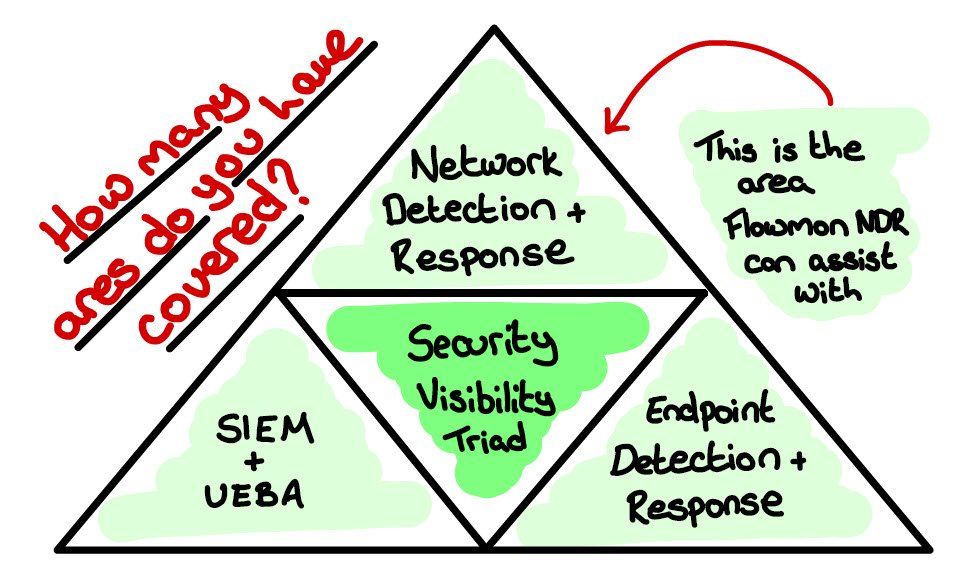
The blurring of boundaries between data protection and security necessitates a unified approach.
Commvault are taking security capabilities used in production directly into their protection platform.
The vital importance of swift recovery, helping organisations minimise downtime and enhance resilience.
Commvault's CTO, David Ngo, then unveiled the latest advancements, each contributing to the company's innovative protection and security solution:
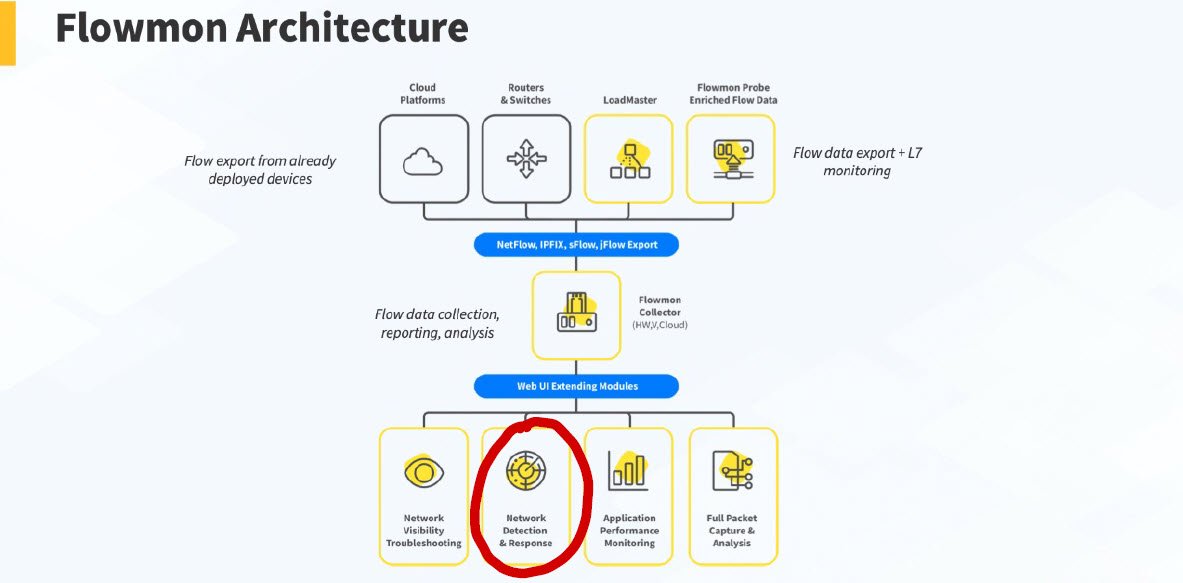
Commvault Cloud Command: A unified dashboard for managing all Commvault services, with integrated visibility into the health, risk levels, security, and recovery.
Commvault Risk Analysis: A machine learning-powered tool that works as a cyber sentinel, securing sensitive data to prevent cyber exposure.
Commvault Threat Scan: A digital detective of sorts, inspecting backup content to quarantine suspicious datasets and ensuring clean recoveries.
Commvault Auto Recovery: This tool tests your recovery readiness and offers forensic analysis to pinpoint clean recovery points.
Commvault Threatwise Advisor: This new feature enables intelligent assessment of backed-up workloads, recommending where sensors should be configured to ensure key data is protected.
One of the event's highlights was an insightful panel discussion hosted by Steve Preston, Commvault's VP for Security. The panel comprised Moriah Hara and Dr. Ed Amoroso from TAG Cyber LLC, Commvault's own CISO, Javier Dominguez, and Yabing Wang, CIO at Just Works. This diverse group touched on a broad range of topics, such as:
The critical role of the CISO in organisations: With the rising complexity of digital threats, the importance of having a strategic leader guiding an organisation's cyber defence can't be overstated.
The AI threat: Imagine a video or voice message that sounds exactly like your CEO but isn't! The panel discussed the dangers of AI-manipulated communication and its implications.
The changing face of risk in the age of COVID-19: The pandemic and the resultant shift to remote working have drastically changed our perception of risk and risk acceptance.
For those aiming to stay ahead of the curve in our evolving digital landscape, Commvault's unique approach provides a compelling solution. By prioritising proactive data protection and security, Commvault demonstrates adaptability and foresight in the face of the rapidly changing cyber threat environment.